
It’s no secret that Windows has, and has, for the majority of its history had a bit of a malware problem.
Every day I read a few headlines about a new threat for Windows users. It seems as though Microsoft has finally had enough of that themselves, what with the recent-ish Crowdstrike bug that took down half the planet for a few days. That event made Microsoft reconsider kernel-level drivers from third-party developers, as they have begun taking measures to avoid any similar incidents from occuring.
Now, Microsoft is focusing on protecting users from lower-level threats to system integrity by introducing what they call Admin Protection.
What about UAC?
You might’ve heard of UAC, User Account Control, a feature introduced back in Windows Vista, which gives users a prompt before allowing programs to have Administrator access to the system.
Well, if you haven’t heard of it, you’ve definitely seen it in action.
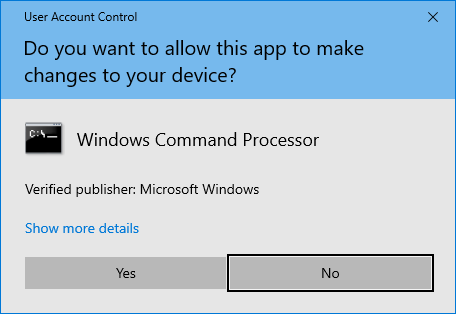
It’s the prompt that shows up to annoy users whenever they install a new application, remove an existing one, or want to touch the system configuration in any way.
At its core it is not unlike Linux’s sudo command. It’s a way to elevate a running programs privileges beyond those of user-land.
So, why do we need “admin protection”?
UAC, is not secure.
Microsoft themselves have stated, at release of Windows Vista, that UAC is not an ironclad security enforcement.
“Vista makes tradeoffs between security and convenience, and both UAC and Protected Mode IE have design choices that required paths to be opened in the IL wall for application compatibility and ease of use.“
said Mark Russinovich of Microsoft’s Platform and Services Division in a Microsoft TechNet blog bost. Neowin’s article about it
If you’re interested in how UAC bypasses tend to work, I’d encourage you to read this blog post by elastic.co, a security research company. It’s very informative, but definitely written for a more nerdy audience.
How is admin protection different?
This is Microsoft’s official showcase of the admin protection prompt
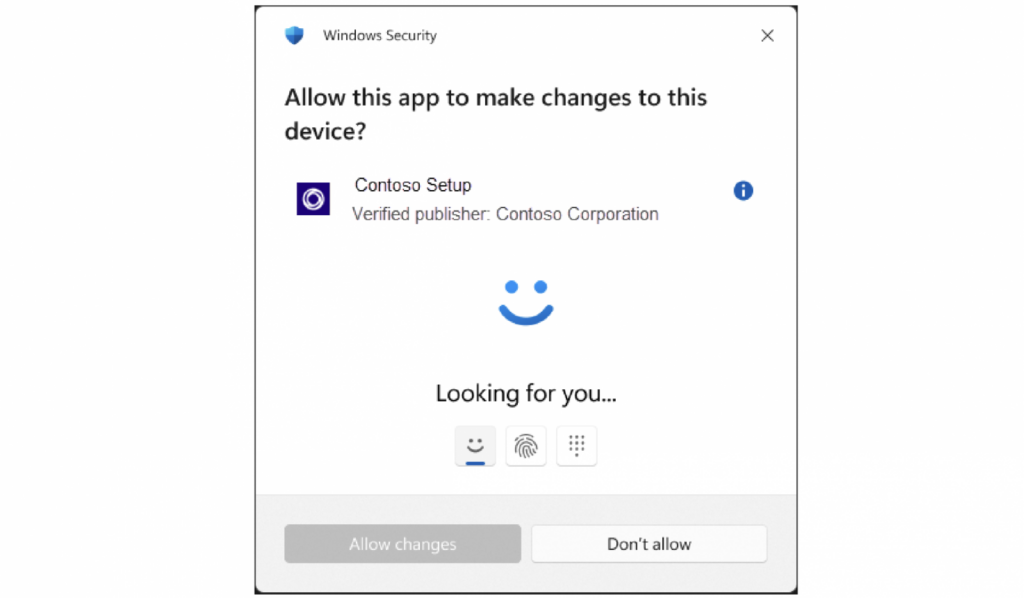
It looks strikingly similar to the UAC prompt, doesn’t it?
The most obvious difference is that here it seems as though Windows wants an additional authentication factor, whether it’s biometrics or a PIN, but this isn’t a new thing. It’s an optional feature that can also be enabled for UAC, but is disabled by default.
No, the biggest differences lie under the hood. The operating system, after getting user authentication via Windows Hello, a supposedly secure way of confirming user actions via different factors, will generate a token that will allow the app in question to perform actions as Administrator.
In theory, the more refined security model offered by admin protection should make sure to harden Windows security just a little bit.
Conclusion?
This doesn’t mean Windows malware will just dissapear. It never will. Even if this makes sure privilege escalation is impossible, if malware developers can get users to click yes on a UAC prompt, then malware developers can get users to click yes and type in their password on an admin protection prompt.
That being said, this is a good step forward for the security of the platform and along with other improvements Microsoft has made to Windows security, like the virtualization-based core isolation introduced a few years ago, along with improvements to Windows Defender tamper protection and other technologies will certainly help at least a bit.
It’s by far not the worst update Microsoft has ever done, if you recall…